Unveiling the Secrets of Windows 10 Logon Events: A Comprehensive Guide
Related Articles: Unveiling the Secrets of Windows 10 Logon Events: A Comprehensive Guide
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Unveiling the Secrets of Windows 10 Logon Events: A Comprehensive Guide. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Unveiling the Secrets of Windows 10 Logon Events: A Comprehensive Guide
In the intricate world of Windows 10, every user action, from a simple file access to a complex system update, is meticulously recorded as an event. These events, stored within the Windows Event Log, provide a detailed chronicle of system activity, offering invaluable insights for troubleshooting, security analysis, and performance optimization. Among these events, those related to user logins, known as logon events, hold particular significance.
Understanding the Importance of Logon Events
Windows 10 logon events chronicle every instance of a user successfully accessing the operating system. This information encompasses not only the user’s identity but also the time of login, the method employed (e.g., password, fingerprint, PIN), and the source of the login attempt (e.g., local machine, remote server). This detailed record serves several critical purposes:
- Security Analysis: Logon events provide a crucial foundation for security monitoring and incident response. By analyzing these events, security professionals can detect suspicious login attempts, identify potential security breaches, and trace the actions of malicious actors. For instance, identifying multiple failed login attempts from an unfamiliar IP address could signal a brute-force attack.
- Troubleshooting: When encountering system issues, logon events can provide valuable clues. For example, if a user reports difficulty logging in, examining the logon events can reveal whether the issue stems from a corrupted user profile, an incorrect password, or a network connectivity problem.
- Account Auditing: Logon events are indispensable for auditing user activity and ensuring compliance with security policies. By analyzing these events, administrators can track user logins, identify unauthorized access attempts, and enforce access controls.
- Performance Optimization: Analyzing logon events can shed light on system performance bottlenecks. For example, observing frequent login delays can indicate hardware issues, software conflicts, or network latency.
Deciphering the Language of Logon Events
Windows 10 logon events are categorized and identified using a standardized system of Event IDs. Each Event ID corresponds to a specific event type, allowing administrators to quickly understand the nature of the logged activity.
Key Event IDs and Their Significance:
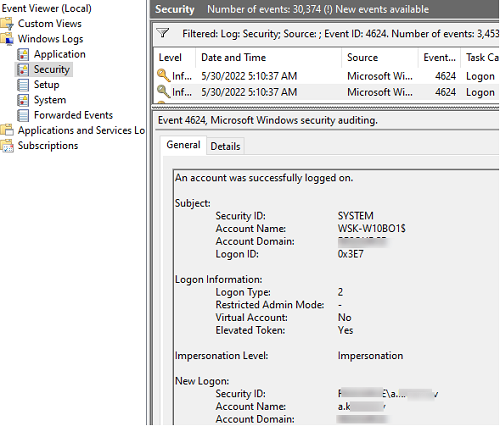
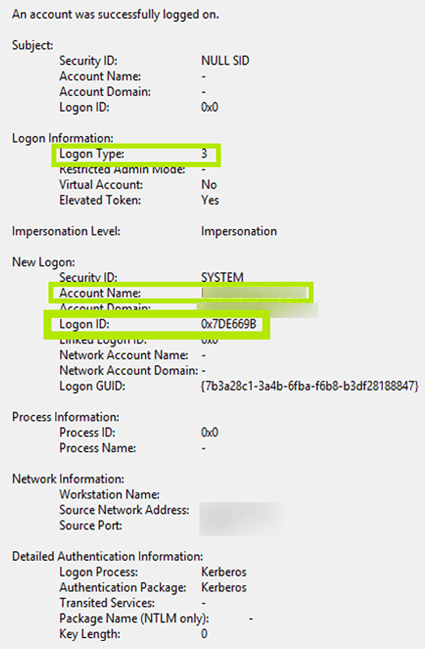
- Event ID 4624: This event, known as "An account was successfully logged on," signifies a successful user login. It includes details like the user’s security identifier (SID), the source of the login (e.g., local machine, network), and the authentication method used.
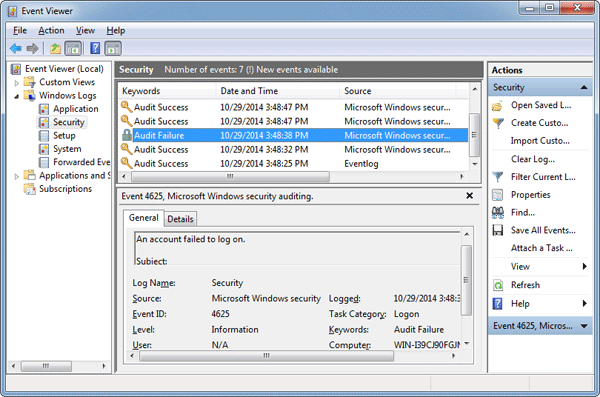
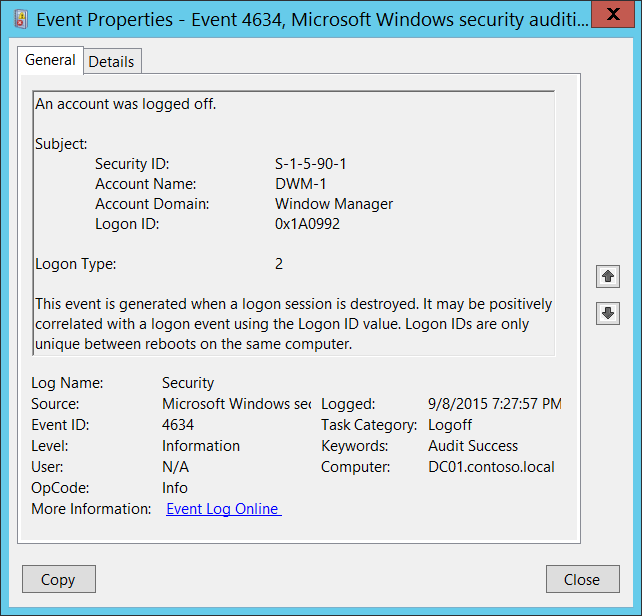
- Event ID 4625: This event, known as "An account failed to log on," indicates a failed login attempt. It includes details like the username, the source of the login attempt, and the reason for the failure (e.g., incorrect password, account lockout).
- Event ID 4768: This event, known as "A Kerberos authentication ticket was requested," signifies a Kerberos authentication attempt, often associated with domain-joined computers. It includes details like the client’s computer name, the requested service, and the authentication outcome.
- Event ID 4776: This event, known as "A Kerberos authentication ticket was successfully renewed," indicates a successful renewal of a Kerberos authentication ticket. It includes details like the client’s computer name, the service, and the ticket’s validity period.
Accessing and Analyzing Logon Events
Windows 10 provides several methods for accessing and analyzing logon events:
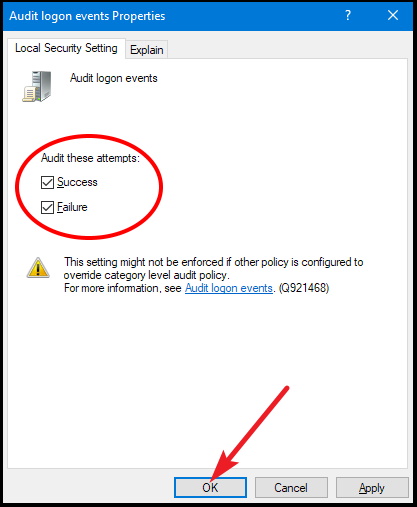
- Event Viewer: The Event Viewer is a built-in tool that allows administrators to browse, filter, and analyze system events. It provides a user-friendly interface for viewing logon events and other system activities.
- Windows Security Event Logs: The Security event log is a dedicated log specifically for security-related events, including logon events. This log provides a comprehensive record of user logins and access attempts.
- Third-Party Tools: Several third-party tools offer advanced features for logon event analysis, including real-time monitoring, event correlation, and reporting. These tools can provide more in-depth insights into user activity and potential security threats.
FAQs about Windows 10 Logon Events
Q: How often are logon events recorded?
A: Windows 10 records logon events every time a user successfully logs in or fails to do so. The frequency of these events depends on user activity and system configuration.
Q: How long are logon events stored?
A: The retention period for logon events is configurable. By default, Windows 10 stores logon events for a limited time. However, administrators can customize this setting to retain events for longer periods, depending on security and compliance requirements.
Q: Can I disable logon event recording?
A: While it is possible to disable logon event recording, it is strongly discouraged. Logon events provide critical information for security monitoring, troubleshooting, and compliance. Disabling this feature significantly compromises system security and reduces the ability to respond to incidents effectively.
Tips for Utilizing Windows 10 Logon Events
- Regularly review logon events: Make it a habit to regularly review logon events, especially in security-sensitive environments. This practice helps identify suspicious activity early and allows for prompt investigation and remediation.
- Configure event logging settings: Customize event logging settings to retain logon events for a sufficient period, based on security and compliance requirements.
- Use filtering and search features: Leverage the filtering and search features of the Event Viewer or third-party tools to quickly identify specific logon events based on criteria such as username, login time, or source.
- Correlate logon events with other system events: Analyze logon events in conjunction with other system events to gain a more comprehensive understanding of user activity and potential security incidents.
- Implement security monitoring solutions: Utilize dedicated security monitoring solutions that analyze logon events in real-time and provide alerts on suspicious activity.
Conclusion
Windows 10 logon events are a treasure trove of information that can empower administrators to enhance system security, troubleshoot issues, and optimize performance. By understanding the significance of these events, their associated Event IDs, and the tools available for their analysis, organizations can leverage this critical data to protect their systems, detect threats, and ensure smooth user experiences.


Closure
Thus, we hope this article has provided valuable insights into Unveiling the Secrets of Windows 10 Logon Events: A Comprehensive Guide. We thank you for taking the time to read this article. See you in our next article!